Security budget of the Cardano project
PoW and PoS have different characteristics regarding the security budget. A PoW network must provide sufficient rewards in every block and it can be a problem in the long term perspective due to the halving. Cardano PoS uses staked coins as protection to the 51% attack and as you will see, it can be very expensive to commit one.
Security is one of the key features of public networks that strive for public trust and higher adoption. In this article, we’ll cover the security budget as it is described within Bitcoin and we will tell you how expensive it can be to attack the Cardano consensus.

What is the network security
The protocol must be resilient to short-term attacks and keep the ledger immutable in the long term. In other words, the protocol must be able to prevent or be able to recover from short-term attacks. In many cases, short-term attack prevention alone is enough to keep the network secure in the long run.
The attacker usually targets the ongoing consensus and is trying to gain a stronger position than that of honest actors. For this purpose, it needs to obtain the necessary means of attack, which are expensive.
As a short-term attack, you might think of trying to spend one coin twice (double-spend attack), attacking the end of the blockchain. An attack on the immutability of a blockchain would be an attempt to rewrite multiple blocks deeper in blockchain’s history. This type of attack would be much more expensive or it would require more sophisticated tactics.
In the article, we will only deal with the prevention of short-term attacks and only from the economic point of view. To be more precise, we will focus mainly on the 51% attack. Note that blockchain security generally depends on many other factors, including the ability of users to use the network safely. For example, there are network attacks where an attacker can attempt to split the network consensus into two parts (also known as chain split). This type of attack may not be as costly as attacking consensus through gaining more dominance. Security is a broad subject, and we will only deal with one part.
The question is what can be done with 51% dominance on the network. An attacker can spend one coin more than once (famous double-spend attack) and prevent some transactions. Network reputation suffers the most. An attacker cannot steal your coins, block all transactions, or change history.
Public networks are natively vulnerable
Traditional financial networks carry large amounts of money every day, and the value of networks of software giants like Amazon, Google, and Facebook is high without the need for a special defense budget. This is because the security of these networks is not so expensive, mainly because of centralization, technical maturity, and a dedicated team of professionals paid by the companies.
Building a security budget is a requirement of public decentralized networks as they are inherently vulnerable to a 51% attack. The network is maintained by volunteers from around the world who are economically motivated to behave honestly. The attack is thus a matter of technical feasibility and cost. The vector of the attacks is obvious. Once the attacker has the necessary amount of money for the attack, he has a great chance of succeeding since he can obtain a dominant position within the network consensus. So the question narrows down to how expensive the attack is.
Security index
For the purpose of our article, let’s define a security index. This will express the ratio of the cost of the attack to the value of the network. If the network were worth $500M and the cost of the attack was $50M, the security index would be 10%. If the cost of the attack were $250M, the security index would be higher, in this case, it would be 50%. A 100% security index would mean that the cost of the attack is the same as the network value. It is probably impossible. Remember, the higher the security index, the better for network security.
Project security is based on coins and almost all cryptocurrencies have one thing in common - whales holding a large number of coins. The protocol should be designed in a way that an attack is as expensive as possible. If the network becomes more economically or socially important and adopted then the cost of the attack should naturally rise. 1% security index means that 1% of the network’s value is sufficient for the attack. Is that enough?

Network value
How to measure network value? This is not easy at all and may vary for different projects and their focus. Moreover, it would be appropriate to combine economic, social, and technological perspectives. Within the article, we will use only the economic perspective. Within cryptocurrencies, it may be the total value of coins, ie market capitalization. However, it can also be the number of active users, that is, the number of transactions in a given period. We can also look at how much value the network carries over a given period, or how much wealth it secures.
As we said, the real value of the network can be very subjective and difficult to measure. We are dealing with the amount that is needed for an attack, so we need the value expressed in money. In our case, we will suffice with the price of coins and the number of transaction fees. Both expressed in fiat currencies.
A network with a certain capitalization can protect much greater wealth, especially if it succeeds in tokenizing real assets. The key question is whether the increased importance of the network will be reflected in the means used to protect against the attack. As you will see, if we only deal with the security budget, it will be sufficient to take into account the market price of a project’s coins and capitalization.
Security budget
Let us first consider the security budget for Bitcoin, as this topic is widely discussed and known. We can then compare the PoW concept with the Cardano PoS. PoW and PoS are quite different in terms of preventing attack through gaining dominance in the network.
The network pays only those participants who behave honestly during making consensus and punish fraudsters. It should, therefore, be economically more advantageous to behave fairly than to cheat. The public network must find sufficient resources to cover security costs. In PoW, the cost of a 51% attack is slightly higher than the value that the network is able to collect to protect itself. The security directly depends on how much money the network is paying out to miners and it is the security budget.

To fit this definition well on a PoS, let’s say the security budget must be big enough to deter attackers. We can perceive the security budget as a minimum amount that an attacker must pay in order for an attack to have a chance of success. Usually, they have to pay a little extra to gain the necessary domination.
Let’s have a look at how the security budget is continuously collected in PoW (neglecting the existence of pools):
- Miner continuously spends energy attempting to find a block. He knows that only honest behavior will result in receiving a reward.
- Once a block is found new coins are released by the network (network subsidy) and transaction fees are also used for the reward. It is actually the security budget for a given short period of time.
- The successful miner receives new coins as a reward so he is able to cover the mining cost and hopefully there is some profit.
It is important to note that the costs of all the miners in the network are approaching, but never exceed the security budget. The network is able to balance itself, and if more miners are involved in mining, mining is less profitable and only those who can reduce their costs (mainly electricity) will survive. It works the other way around, if mining is more profitable than it is normally (in case of the balance), new miners will come.
The security budget consists of newly created coins and transaction fees:
security budget = new coins + transaction fees

Security of Cardano
The security of public networks is not governed by a centralized authority. It is something that evolves organically with the growth of projects. Let's have a look at how secure Cardano is. Read more
To motivate miners to behave honestly the security budget must be higher than the cost of mining to satisfy miner's needs and provide margin. Let’s look at how high the annual security budget should be:
hardware cost + operating cost ≤ security budget
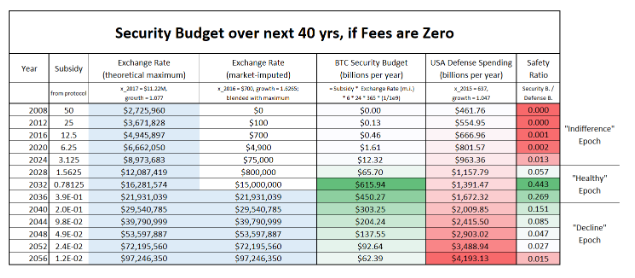
Let’s simplify the calculation to calculate your daily security budget (let’s neglect the price of the ASIC miner). Bitcoin adds 144 new blocks to the blockchain per day. The reward for the block is 12.5 coins at the beginning of the year 2020. The network releases 1,800 new coins per day for its security. The market price of coins at the time of writing is $8700, so the network has $15 660 000 per day. If all of the blocks were 1 MB in size, each block would hold ~4,000 transactions, which is about 600,000 transactions per day. At the time of writing, the transaction fee is $0.5. The network will collect an additional ~$300,000 on fees. Note that the amount of money collected on the fees is much smaller than the number of new coins. The network has a total of about $16M in the security budget every day. This is at the same time the approximate cost needed for the one-day long attack.
We simplified our calculations and did not take into account the cost of hardware that would make the attack more expensive. On the other hand, hardware or hash-rate can be rented and we can assume that the attacker already has the hardware. It should be noted that the cost of specialized hardware can drop significantly after an unsuccessful attack since it has no other use.
Notice that we cannot talk about absolute hash-rate. It is irrelevant. It is not true that the higher the hash-rate, the safer the network. The hash-rate rises due to technical innovations of ASIC miners and also due to the rising price of coins over the last decade. The attack is really only about money and security budget.
We can conclude that the higher the security budget is the higher is security.
Let’s have a look at the security index? The current Bitcoin narrative is that it’s a store of value. We can, therefore, use the current capitalization of the project because a successful attack directly threatens the price of coins. The current capitalization of the project is $ ~160,000,000,000. Security index is ~0,01%. This value is valid provided that the attack succeeds in 1 day. 144 blocks should be enough for a successful attack.
Scalability of a security index
The capitalization and utility value of the network increases with adoption. This is reflected in the increasing number of transactions, the size of the transmitted value, etc. It would, therefore, be desirable for the security budget to grow as the value of the network increases. However, this is the opposite of what halving does.
Halving is a mechanism that halves the number of rewards every 4 years. In 2020, network subsidies will decrease from 12.5 coins to 6.25. This means that the security index will be halved along with the security budget if the market price of the coins remains the same. If the price of coins doubles, both values ​​will remain at the same level. In 2028 the reward will be 1.56 coins and in 2032 it will be 0.78 coins.
PoW networks generally have a big problem with scaling on the first layers and solve it mainly through the second layer. The number of transactions on the first layer is likely to remain the same. However, only transaction fees could potentially increase the security budget as the network subsidy decreases in time. If the number of transactions is low then only fees will probably rise.
Miners and users would benefit from high security and it could be expected that users will be willing to pay high fees to miners. In reality, however, nobody wants to actually pay expensive transaction fees. We have here a typical tragedy of the commons problem. Read the following article to learn more: https://www.econlib.org/library/Enc/TragedyoftheCommons.html
The security index in PoW networks does not naturally scale in time, as adoption and higher usage are expected to rise. Network security is fully dependent only on the market price of coins. So in order to secure the network, the market price of coins must necessarily rise. In the real world, nothing grows into heaven, and relying on price increases is very unreliable and treacherous.
Bitcoin has the ability to outperform its ATH. On the other hand, the bear market is usually followed by a slump of 80%. If we see the price of $100K per coin, it is likely that we will then see $20K. The attacker theoretically has the opportunity to try to knock down the total capitalization before the attack, thus reducing the security budget. Moreover, by selling coins, he gets the necessary cash for the attack.
The bitcoin security index is not too high and will probably not improve much over time. The cost of the attack will always be significantly lower than the capitalization of the project. In the past, we have seen successful attacks on smaller PoW projects. The cost of a Bitcoin attack is far too costly and the current security budget seems to be sufficient.
Security budget of Cardano PoS
In the PoS system, the network is owned by all stakeholders through holding coins. This feature can be beautifully used for network security. The attack on the PoS is possible only through coins and in the case of Cardano, the attacker needs to accumulate more than 50%. The PoS network does not have to directly maintain a security budget to pay for its protection via block reward. Basically, the security budget is always present through all coins that are used for staking. How to calculate the cost of an attack?
cost of an attack > ~staked coins / 2
The cost of the attack is greater than half of the staked ADA coins. It can be assumed that the majority of the coins will be used for staking, but not all will. If the coins do not participate in staking, they will probably be locked elsewhere (e.g within some Decentralized Finance project). Technically they will reduce the cost of attack. However, the attack will not be necessarily cheaper, as these coins will not be easily available on the market if they are used.
In addition, if an attacker attempts to aggressively buy coins on the free market, the price of coins will rise. This makes the attack even more expensive. How much it is? The calculation is very simple. The price of a single ADA coin is $0,045 at the time of writing. The capitalization of the Cardano project is $1,174,917,869.
The cost of the attack will be higher than ~$500,000,000 if the price of coins remains the same during the purchase by one entity. Well, if only 1/2 coins in the circulation will be used for staking, it will be ~$250,000,000.

The security of the Cardano network depends just like Bitcoin on the cost of coins. However, all coins in circulation constitute a security budget, and a rogue entity must purchase these coins. Security is therefore mainly based on the distribution of coins between users and the desire to hold and not sell to the attacker. This protects the network itself. The motivation to hold coins goes hand in hand with real usability, the rising market price of coins, or the ability of a project to pay stakeholders. Mainly passive income will motivate stakeholders to hold ADA coins. The network will have a subsidy budget for the first 10 years of operation as the number of transactions could be initially low. However, Cardano is striving for high scalability of transactions, and in the future, it will be able to accumulate a large number of coins for rewards and the project treasury. There is no need to pay for energy in PoS, so once pool operators take their margins, the rest can be paid off to stakeholders.
Let’s have a look at how security mechanic works:
- The network offers a lot of interesting features and services for people to use it. The network is scalable, thus it is able to collect a satisfactory large number of coins for the stakeholders rewarding.
- Pool operators and all delegators are rewarded for holding coins. Passive income is a good reason to keep coins. Since nearly nobody is willing to sell coins cheaply there is a high demand on the market and the price of coins rises.
- The rising price of coins makes an attack very expensive and scale with growing project capitalization.
- An attacker must buy 51% of all staked coins and they get more and more expensive as there is a shortage of them in the market.
- The attacker will find out that he puts his coin into danger if he will try to make an attack. He is attacking mainly himself.
The security index is always at least ~50% of staked coins. The attack is very costly and most importantly, the attacker has his own skin in the game, as he will have to hold most of the coins himself for the attack.
As for the security index scaling, it grows as network adoption and usability increase and it will have a direct impact on the capitalization of the project. It can, therefore, be assumed that the security budget will be increasingly higher.
It is needed to realize that it is not needed to issue so many coins in order to reward participants since there is a lack of high electricity consumption. To maintain the network is basically very cheap. Thus the network might motivate all stakeholders by giving them part of collected fees. In other words, the network can economically motivate users to keep coins and thus support higher decentralization. PoS can use a wide array of techniques to better prevent centralization and discourage the forming of centralized cartels.
People sometimes criticize PoS for being cheap to make a block. As you can see, this does not compromise security.
Comparison Bitcoin PoW and Cardano PoS
In the case of PoW, it was not a very smart design decision to rely on the market price of the coins if the amount of coins in the security budget is decreasing over time and there is no other mechanism to fill in the budget.
Satoshi told to it:
In a few decades when the reward gets too small, the transaction fee will become the main compensation for nodes. I’m sure that in 20 years there will either be very large transaction volume or no volume.
Satoshi hoped the scaling would be somehow resolved. If scalability will be resolved only in the second layer networks, Bitcoin’s first layer will be hurt economically. The time for a solution is getting shorter and the team will certainly have to resolve it before 2140. In 2032 the reward will be only 0.78 BTC. For example, if a single BTC is for $250,000 the security budget will be~ $28,000,000 per day.
Cardano PoS also relies on the market price of the coin, but always has at the disposal approximately half of its market capitalization to defend itself. If the price of ADA coins gets over $1, the security budget will be ~$15,000,000,000.

The security index speaks clearly in favor of Cardano, as it might be ~50%. Bitcoin will struggle to get to 1%.
Another advantage of Cardano is that the project has its treasury, into which part of the transaction fees will go. Projects will always have their technical problems and the solution is straightforward. The project needs finances and capable people to actively solve problems. Only then can the project survive in the long term.
The security index of Bitcoin does not necessarily scale with higher adoption and market capitalization. Even if the capitalization goes higher due to the halving the security budget might not be as big as would be expected from the point of view of the security index. Cardano’s security scales naturally with adoption since the increase of capitalization makes an attack proportionally more expensive.
The higher the decentralization of a project is the more secure will be the consensus since it is more difficult for participants to join the effort to attack the network. So it is not only about the absolute cost of the attack. Whales in the system can participate in the attack or their power can be misused.
Summary
It’s not very smart to attack the strongest point of the network. It’s better to find a weakness, like a code vulnerability. The cost of the attack can serve as a very good prevention. Technically, however, the attacks cannot be prevented. The network must take care to prevent attacks and the only way is sufficient economic motivation. Public networks will grow in importance, and security will be one of the qualities that everyone will explore before they trust the network. Currently, public networks are not important and not adopted. Imagine, however, that they will form the foundation of the financial world in the future. Their value or meaning will not only be economic but also social and political. Such a network may be the target of an attack by a hostile state. Security is therefore always in the first place.
Bitcoin works well over a decade and the connection to the physical world and energy consumption works so far very well. However, the question is whether this system is sustainable in the long term. The team does not have a clear solution yet and we see rather quarrels and opinions of individuals. Cardano will need some time to prove that it can work well without energy consumption. This is definitely worth the higher scalability and decentralization.
PoS is able fo better scalability of transactions so it might collect a big number of coins. However, it is important only to attract people to own ADA since the more transactions the more profit for stake-holders. That indirectly makes the attack very expensive. PoS does not need to directly build a security budget. It is sufficient to strive for adoption to keep the protocol secure. It can be said that network scalability also helps security.
The decentralization increases security since it is more difficult for participants to join the effort to attack the network. A high level of decentralization is needed as protection from the participants from inside of the ecosystem. E.g, what if 3 bigs whales (pool operators) join the effort in the PoW network? They might dictate to collect tax as we saw that in case of Bitcoin Cash project: https://www.ccn.com/bitcoin-cash-community-fractured-by-sudden-12-5-mining-tax/
The Cardano team could learn from the mistakes of existing protocols and do some things differently. The team had more time to think, design, and test different concepts. Everything was driven by research. The security budget is one of many examples of how to elegantly solve some problems technically and more reliably.
