Cryptography for Cardano Wallet Users
If you own any crypto then you should know how to protect your wealth. It can be a challenge if you are not an IT guru. We can help you and teach you the basics of cryptography.

Asymmetric cryptography and hashing functions are a complex topic for ordinary users. However, anyone who wants to use a cryptocurrency wallet safely should know the basics. We will not discuss how exactly and why cryptography works. We will explain the basic principles of cryptography from the perspective of wallet users. We tell you how cryptographic tools are usually used. There will be some theory in the article, but we promise, no math. We will try to find analogies that facilitate understanding. The article does not aim to be comprehensive and terminologically accurate.
If you want to keep your ADA coins safe, you need to learn basics. As you will see, you don’t have to remember that much. If you don’t want to deal with theory, look at least at the last section dedicated to wallets.
I have heard something about a key
Cryptography is the practice and bunch of techniques for secure communication in the presence of third parties called adversaries. Cryptography is about constructing protocols that prevent third parties or the public from reading private messages and data. It also deals with various aspects of information security, data confidentiality, data integrity, authentication, and non-repudiation.
Most users probably use cryptography for converting ordinary readable plain text into unintelligible, unreadable text (just a “mess of characters”, also called ciphertext) and vice-versa. Imagine that you have some text and you don’t want someone else to read it. It’s your secret you want to protect. At the same time, you want to be able to easily access the original form, or send the secret over the Internet to someone else and allow him to read the document.
Once the original text is converted into an unreadable form, nobody is able to deduce the original form. The content of the document is thus safely protected from misuse.
The conversion process, when a readable form of a document is converted into the unreadable form, is called encryption.
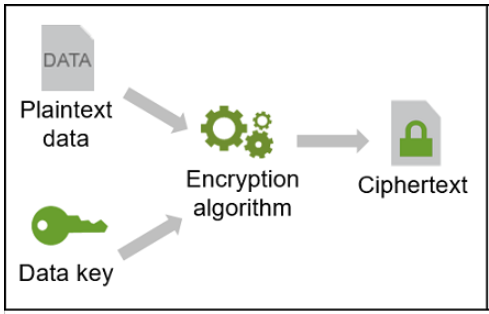
The opposite process of making illegible forms readable again (the original form is recovered) is called decryption.
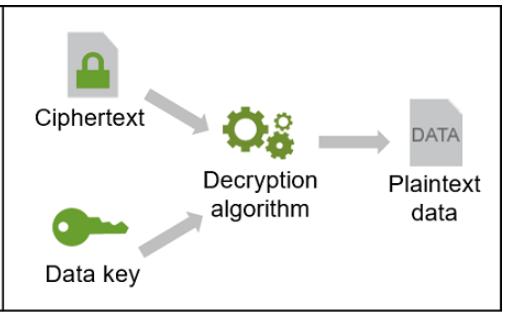
Let’s say that I have some secret written in a document (just a file). Cryptography allows me to convert the document into an unreadable format (encryption) so I can have it on my computer or send it via the internet to somebody else. The point is that nobody else is able to read it. If I want to let somebody else read the document I have to provide him with the secret. Only I know the way how to convert unreadable form back into a readable document. It means, restores back the original form of the document.
The conversion process (encryption) needs three things:
- A cryptographic algorithm, what is basically a function that takes some parameters as an input to produce output. The algorithm is based on complex mathematics and you can imagine it as a set of rules that dictate what to do to convert the original text into an unreadable form.
- A digital input that is to be converted into an unreadable format. It can be a file or plain text. It is what should be protected.
- A cryptographic key. The cryptographic key is a piece of information that determines the output of the cryptographic algorithm. In addition, the key is used for the reverse process and makes it possible to restore the original form. Without the key, there would be no chance to restore the original form after encryption.
Notice, that the cryptographic key and file are inputs for the cryptographic algorithm. The algorithm behaves always the same. Different inputs for the algorithm results in different outputs. If you choose to encrypt one file multiple times and use a different key each time, you will receive different encrypted texts (ciphertext). For example, you can use key A and key B to produce ciphertext A and ciphertext B. Both ciphertexts are significantly different despite the input file was the same. Used key made the difference. To decrypt ciphertext A only key A must be used. Notice that using key B to decrypt ciphertext A will not produce readable text.
Once the cryptographic algorithm produces a result ciphertext you can delete original data in the plain text including all copies. You are able to get the original file again from the ciphertext via using the key. So you have to keep the key in a safe place!
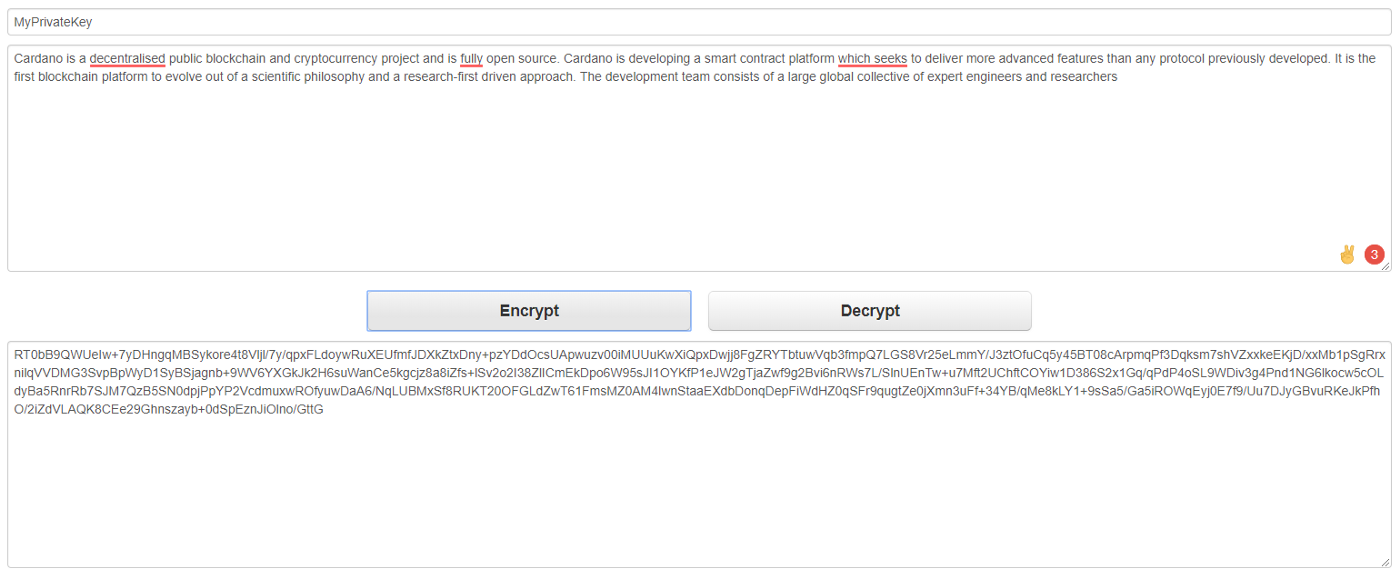
Is it complex? Think of the encryption process as a meat grinder. When you put the beef meat and a bit of salt into the meat grinder, the mash comes out. Eating the mash you have no chance to recognize that beef meat was used as an input. When you put the pork meat a bit of salt, the mash comes out again, but a different one. However, the taste of the mash will be very similar to the previous one.
The inserted meat and salt determines the quality of the mash. The meat grinder represents the cryptographic algorithm. The meat is a readable input (text) and salt is a cryptographic key. The mash is the unreadable output. Every piece of meat and salt is unique so the output mash is unique as well.


The cryptography behind Cardano blocks
Cryptocurrencies could be invented due to the many major achievements in cryptography. It is not a surprise that cryptography is used not only for signing transactions but it is also used for the creation of new blocks. In the article, we will have a look at how a new block is created in the Cardano network from the point of view of cryptography. Read more
Unlike a meat grinder, cryptography can also reverse the process to restore back the original meat from the mash (including the original taste). To do so, you need the mash and the same amount of salt that was used to create the mash. The process can be repeated over and over (you can encrypt and decrypt more times in a row).
If an attacker sees only a mash he has no chance to deduce how the meat or salt looked like. To get original meat, you need to know the combination of mash and salt. In other words, you need to exactly know which salt was used to produce the mash from which you want to make the original meat. Having just mash or salt is useless. Thus you can put the mash on the table and everybody can see it and taste it. Without the exact amount of salt, nobody is able to deduce that the original meat was 1,254 kg of beef.

You can imagine the algorithm as a piece of source code that anybody can or potentially could see, so it cannot be secret (at least you cannot trust it). So the cryptographic key must be the secret. The key allows you to change plain text into an unreadable form via using the algorithm (encryption) and using the related algorithm for restoration (decryption).
Let’s try another analogy to explain the key. There are many doors in the world that keep a secret. Only the one who has the key can get to the secret via unlocking the door. Only a holder of the key has the right and possibility to open the door and step inside. The key opens the secret.
Key security and uniqueness are influenced by its length. In general, the longer a key is, the better security it provides assuming that it is generated truly randomly. There is a huge amount of numbers in the world so the longer the key, the higher is the possibility to generate really unique key. The length of the key directly affects also the difficulty of the so-called brute-force attack.
A brute force attack, also known as an exhaustive search, is a cryptographic hack that relies on guessing possible combinations of a given cipher until the correct combination is discovered. The longer the key, the more combinations that will need to be tested. We said that the key length is about numbers so the longer key is the more numbers must be tried to break it. A brute force attack can be time-consuming, difficult to perform if methods such as data obfuscation are used, and at times downright impossible. Within this article, you do not need to deal with the attack. Just keep in mind the rule: the longer key the better security.
Remember, a private key is what you always need to keep secret. The word private means “yours”. It is a secret that must not come to anyone else’s hand. Otherwise, the secret can be revealed.
Asymmetric cryptography
Asymmetric cryptography, also known as public-key cryptography, uses two keys. A private key and a public key. It also called the key pair. The key pair always work together. So there is a private key A and related public key A. Besides that there can be private key B and related public key B. And there are many more key pairs. The point is, that private key A and public key B cannot be combined in a sensible way.
There is a certain key generation process that firstly generates a private key and secondly, based on the private key used as an input, it generates also public key. The keys generation process is also a kind of cryptographic algorithm that requires an input to generate a key. So you, as a user, have to provide some input that is used as the input. The input can be either a random number or a piece of text you remember. Alternatively, some tools can make it for you (provide some randomness) and you just have to keep the private key safe. We will get back to the key generation and needed input later.

As the name suggests, the private key is a secret that must not be revealed to anyone else. On the contrary, you can freely publish the public key and do not have to worry that somebody else will see it or try to use it. This is the magic of asymmetric cryptography. You can send or reveal a public key and share some secrets or do other interesting things. The safe propagation of the private key to somebody else is quite a dangerous process.
Remember, that it is possible to use a private key again to generate the same public key. Conversely, it does not work. It is not possible to derive the private key from the public one.
There are more possibilities on how to use asymmetric cryptography, but we will only show the one that interests us the most within cryptocurrencies. It is a digital signature.
We will simplify the explanation only to the basic principle important for understanding. The digital signature is used in a way that any recipient can verify via a public key that a received message has been sent by the private key holder. The private key holder may disclose his public key to anybody who is interested to verify the authenticity of the message. Once the message is signed with the private key, anyone in the world holding a paired public key can verify that the message has been sent by the private key holder.
Alice, the private key holder, can say: “I am Alice and this is my public key. Once you receive a message you can verify that it is really from me via the public key. Here you are.”. Bob is interested in the verification. So he waits for messages and uses Alice’s public key for authenticity verification. Nobody else in the world is able to sign the message properly unless the private key is not compromised, meaning stolen from Alice. We will come with a more precise explanation later.
Hashing
Let’s introduce another operation or function that is used in cryptography, which is hashing. Hashing is again just a process or a function provided by some tools. Imagine it as the usage of a certain algorithm that takes some input and produces output. It is similar to the meat grinder, however, there is no key in play now. There are only one input and one output.
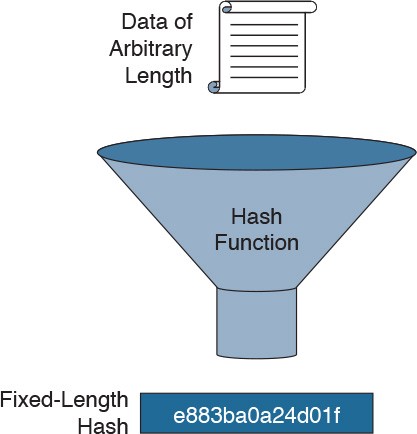
A hash function takes arbitrarily large data as an input and makes a digital fingerprint that is usually shorter. There are more names for the fingerprint, you can hear about hash, hash code, digest, etc. Producing a hash is a very fast process regardless of how big input data are.
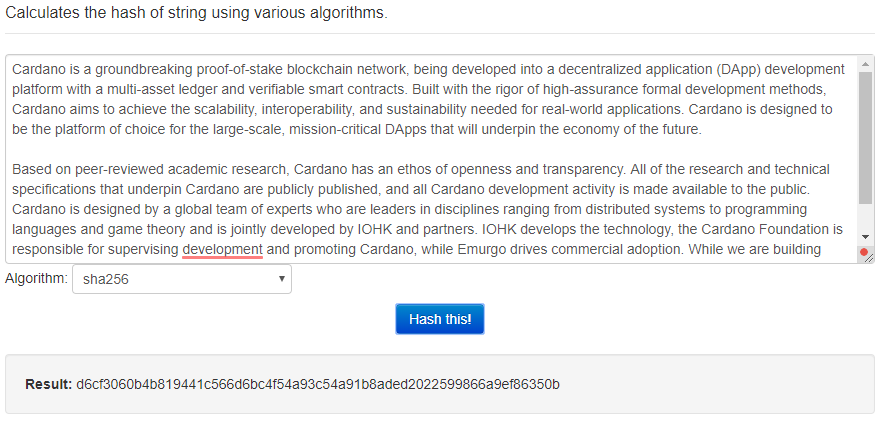
As you can see below in the picture, we provided quite a long text as an input for the SHA256 hashing algorithm. The digest is just following string:
d6cf3060b4b819441c566d6bc4f54a93c54a91b8aded2022599866a9ef86350b
It does not matter how long or big the input is. The digest has always similar length.
Hashing is defined by two distinct characteristics:
- Irreversibility ensures that once a hash is produced there is no way how to get original data (input) from the output (hash/digest). In our analogy with the meat grinder, you can always easily make mash from meat. But it is not possible to make meat from the mash. Moreover, you can put 50 tons of pork meat into the meat grinder and output will be only 10 grams of mash. Meat represents the input (data, file, text). Mash represents the hash (digest). The meat grinder is the hashing function.
- Uniqueness points to the fact that for different data a unique hash is always produced. Even if you had a book and changed only one character the hash would look quite different. If you had a stake and try to produce a mash then the mash would be always the same. Of course, in reality, once a stake goes through the meat grinder it makes no sense to try it again. It is, however, possible with digital data.
If you repeat the hashing process over and over you will always get the same hash for the same input data. Once the original data gets lost you cannot produce the hash again and it is not possible to restore the original data from the hash.
This feature is used to validate data authenticity. For example, your friend Carol wishes to send you a file and wants to make sure you get the original. Carol will make a hash and send it to you via Messanger, or publishes it on her website. Carol will then send you the data. You can make a hash of the received file and you can compare whether it is the same as Carol’s one. If both hashes are the same then you have received original data. If not you have received a fake data.
Notice that it is often used for downloading software from the Internet. An author of software can publish a hash on the web nearby the file for downloading. Thus, users can verify that they have downloaded the correct file.
Be aware of the difference between hashing and asymmetric cryptography. Within hashing, data are not considered as secret and after applying hashing function the data still keeps the original form. There is no conversion (no encryption). Hashing is used for verification of authenticity. Asymmetric cryptography is used to protect the original data form or to ensure that a sender of a message is also the holder of a private key. So you have some secret (private key) that allows you to encrypt original data or sign a message.
Alice and Bob reloaded
Do you remember the example above where Alice sent a message to Bob? Let’s correct it a bit. It is important to ensure that the message itself was not changed by somebody during the way from Alice to Bob. The message is not the secret that Alice wants to protect. Moreover, Alice wants to prove to Bob that she sent the message and owns the private key that corresponds to the public key.
A digital signature is a piece of data that is attached to a message and is used to verify whether the message has tampered during the transmission over the internet. So to ensure message integrity (hashing is used). Moreover, the author of the message can prove authenticity (asymmetric cryptography is used).
The digital signature is generated in two steps process where both hashing and asymmetric cryptography are used. A digital signature is an encrypted hash of the message that Alice wishes to send.
To sign a message, Alice will do the following.
- Alice applies a hash function to the message to produce a hash (digest).
- Alice uses her private key to encrypt the hash. Be careful, not the message.
- Sends the message to Bob together with the digital signature.
Bob receives the message with the digital signature and will do the following to verify message integrity and authenticity.
- Bob uses the public key (that received earlier from Alice) to decrypt the hash. In other words, the hash will be readable again (it is still a collection of characters).
- Bob applies the same hash function (same as Alice used) to the received message to produce hash (digest).
- Bob compares both hashes. Decrypted hash from Alice (the one that was part of the message from Alice) and the hash, that Bob obtained by applying the same hash function to the received message. If both hashes are the same then Bob is sure that the message was sent by Alice and the content of the message is authentic. If hashes are not the same than something wrong happened and the message was tampered by a third party. Bob does not trust the message.
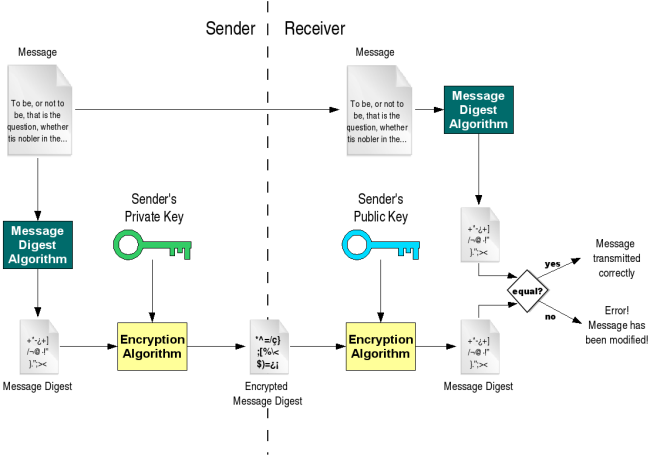
In the example, the digital signature was used to ensure the integrity and authenticity of the message. Bob could ensure that the message was really signed by Alice and the content is the same as Alice wrote it. The message was not encrypted and anybody could read it. Alice did not want to keep the message private but it is easy to do so. If Alice wanted to add privacy she could encrypt the message as well and Bob would have to decrypt it. The base principle with a digital signature would remain the same.
Crypto finally
Now we are finally moving from theory to practice. Ownership of ADA coins is established through private keys and Cardano addresses. It is needed for providing a digital signature. The network does not directly work with private keys, it just checks the digital signatures. Only holders of private keys can initialize a transfer of ADA coins from a given address. The transfer is realized via transaction. Users have to take care of their private keys since only that allows spending of ADA coins.
Cryptography is always used through appropriate tools. In the case of cryptocurrencies, this is realized by wallets. Remember, wallets store your private keys, so ownership of ADA coins is always as safe as your wallet is safe. Private keys are used for signing transactions so there is no need to reveal private keys to somebody else on the Internet! The Cardano network does not need your private key for the transfer of ADA coins. Nobody else in the world should care about your keys.

We have explained how digital signature works and a very similar procedure is used to send ADA coins from your wallet to somebody else to his/her address. The transaction represents the wish of the current ADA coins owner to transfer them to another address. Cardano transaction requires a valid digital signature. The network needs to verify the ownership of ADA coins to include the transaction into the blockchain and to do so, the digital signature is checked. Only the owner of the private key can sign a transaction that transfers ADA coins from one Cardano address to the recipient address. In other words, spending funds from a given address requires ownership of the corresponding private key. There is a relationship between a private key and address and we will explain it a bit later. Signing a transaction to spend funds is called a witness. Witness data is proof that the owner of the private key decided to transfer funds.
The process of spending ADA coins from a user perspective looks like this:
- A user creates a transaction and defines how many ADA is to be sent.
- The wallet selects coins sitting on an address (let’s make it simple for now, it is UTXO) and uses an appropriate private key to sign the transaction.
- The transaction is sent to the network.
- A node decides to add the transaction to a block. The node verifies the digital signature (and does many other checks). After then it adds the block to its own blockchain.
- The node propagates the block to other nodes.
- Other nodes verify the block including all transactions and decide whether to put the block into their blockchain.
- If the majority of nodes added the block into their blockchains then the recipient can see ADA coins on his/her address.
Remember, if a private key is lost then nobody is able to spend funds from an address. The network cannot do it since it is not able to verify the digital signature. Technically speaking, clients follow rules that are defined by programmers in the source code. Thus, ADA coins will never be spent and will sit on the address without the possibility to be transferred forever if a private key is lost.
Cardano, like other cryptocurrencies, uses asymmetric cryptography. So there is a key pair. A private key and corresponding public key. Now the magic comes. The public key is used as an address on which some ADA can be sent. The corresponding paired private key is used to spend the ADA coins from the address. You can imagine that a public key is an account and private key is a password needed to spend coins.
Always when a wallet creates a new address the key pair is generated. Firstly, the private key is generated and from it, the corresponding public key is created. The public key is then used for the address. The public key might not be necessarily used as-is. The public key representing address might be hashed as another layer of security (in order to save space, it is preferable to use the shortest possible addresses).
When a transaction is created the public key of the address from which ADA coins are to be sent and a digital signature is needed for everyone in the network to verify it. Part of the transaction must be also the recipient address since the ADA ownership moves from address to address. From one’s private key owners to another. However, you can send ADA to yourself.
A node that creates a block includes the transaction into the block and validates the digital signature. When the block is propagated all full nodes validate the whole block and all transactions included all digital signatures. If a digital signature is correct and all other checks passed, then ADA coins will be transferred.
The wallet always stores all private keys for all addresses. If you generate 10 addresses then there are generated 10 private keys and 10 public keys. You, as a Cardano user, are lucky that you never need to operate with private and public keys directly. Your wallet does everything for you. You just need to use addresses. You never need to see private keys. If you do not know private keys then there is less probability that they will be stolen. For the security of your coins, do not try to see your private keys.
So where is the secret you should keep hidden? Remember, everything you need is the wallet seed or passphrase!
A seed might be a number or a few words (12, 24, …) that is used as an input for the creation of a private key. Let’s call it a root private key. The root private key is used by a wallet to generate all other private keys. What is important here is that there is a deterministic process that generates always the same root private key for a given seed. In other words, from the same seed always the same root private key is generated.
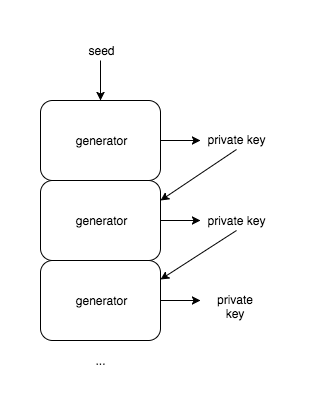
The following picture describing BIP 32 can also be helpful. You can see the basics principles of how Bitcoin wallets are supposed to work:
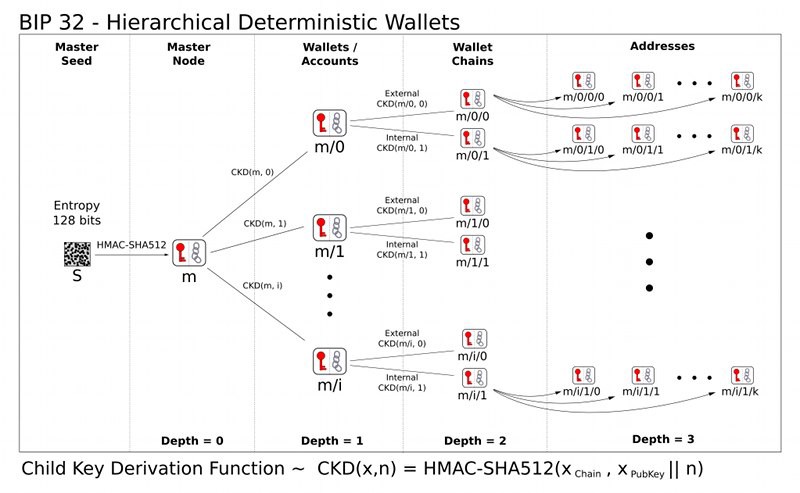
Once you know the seed you are able to use the same process to generate all other private keys needed for signing transactions and of course all addresses. Thus, you can lose your cell phone, your computer might not start one day, or your hardware wallet might be stolen. It does not matter if you remember and have safely stored the seed. You are still the owner of all ADA coins since you can install the same wallet (or even another wallet) and restore your root private key including all private keys and addresses. ADA coins will stay sitting on the same address in the blockchain until the private key is used to spend them. At any moment, the network knows at which addresses all coins are. Coins can never be lost. What can be lost is only a private key that allows spending. So the only private key owner can fail. Not the network.
That is why you are always instructed by the wallet to safely store the seed and type it again to verify that you have written it down correctly. Seed should be ideally written on the piece of paper. Once you have a seed, everything can be restored.

Remember, all you need to safely store is the seed. Never provide the seed to somebody else since once an attacker knows your seed he can easily restore your wallet and spend your ADA coins. During the wallet restoration, a root private key is generated, and then all private keys one by one. The first private key is generated, then the address and it can be verified that there are or have been some coins on the address. If it is the case next private key is generated and the process repeats until a few empty addresses are met. It means that you have not used more addresses. The generation of private keys is also a deterministic process. For example, incrementing a number is sufficient to generate another private key.
Coins ownership
Let’s look at one interesting detail related to coin ownership. Information on which addresses the ADA coin is currently in is always stored in the blockchain. So ADA coins can never be lost from the point of the blockchain. The network, through distributed clients, does only what the developers have written into the source code. Essentially, the source code dictates the conditions under which coins can move from an address to another address. One of the conditions is to provide proof that the real owner moves the coins. The owner must have a private key to the address to prove ownership and the proof is part of a transaction. All clients can easily verify that and refuse to add the transaction into a block if there is not appropriate ownership proof. No one is able to force the spending of coins without an appropriate private key. If the majority of nodes in the network use the official and unmodified client (created from public open-source code), none other than the owner of the private key can spend coins. Blockchain is just a database for storing information about coins. A distributed algorithm in clients is involved in the transfer of coins, and it needs proof that can only be provided through a private key.
The Daedalus wallet just read the blockchain from the beginning (all blocks) and once it gets synced (all blocks were read) it displays your balance. The wallet does not store any ADA coins. The wallet works only with private keys that are needed for spending coins from given addresses via transactions. The distributed network algorithm will check the transaction and if the proof of ownership is correct then ADA coins can be spent.
Do you remember that it is not possible to create a private key from the public key? In the context of blockchain, it is not possible to create a private key (needed to sign a transaction) from an address. You can know the address where you have coins and you can see it for example on a blockchain explorer. However, you just see what is written in the ledger. It is still a question whether you have also the paired private key. You own coins only if you are able to spend them. If you have a wallet and do not know the SEED then you lose coins in the case you cannot use the wallet for any reason. The reason is that you are not able to restore the wallet and all private keys when something wrong happens.
From a user point of view, the coin owner is only the one who is able to spend it. So the owner of private keys.
Summary
If you should remember one thing from today’s article, it should be this. Protect your seed and never give or show it to anyone. Only then you will remain the owner of your ADA coins.
You could hear the sentence: “Not your keys, not your coins.”. As we said, you probably never see your private keys so the seed and own wallet are the most important things. The sentence was probably used in the context of exchanges. If you have your coins on an exchange then you are definitely not the owner of coins. You just have credentials to log in to the exchange and you have to hope that the coins will be there next time. You just trust the exchange.
We could provide more information, but there was enough for one article. Next time we look at specific things in more detail.
